Overview of ShipExec™ Installation
The ShipExec™ team designed ShipExec™ for users inside and outside your company’s network. The components and installations are designed so that some of the components can be inside the network, and internet facing components can be installed in what we will refer to as a demilitarized zone (DMZ). If your company is installing ShipExec for use inside your company’s firewall only then this may seem like overkill, however security inside your firewall should be just as important.
With that in mind, the ShipExec™ development team is constantly working to ensure that all communications are secure. This requires that we use Transport Layer Security (TLS) 1.2 or greater with HTTPS with a certificate from a certificate authority. ShipExec™ also use a certificate with a private key for communications with our client APIs. This can be the same certificate used for HTTPS or a separate certificate.
The ShipExec™ components can be installed on separate systems or can be installed on just a couple of systems depending on the volume and type of shipments and the complexity of the business rules required. In the ShipExec layout diagram (Figure 1-3), we will show several separate ways to layout and distribute the workload for the ShipExec™ system.
When setting up ShipExec for an enterprise, a distributed install with multiple servers is recommended (Figure 1). The Scheduler server is a single server requirement. The SQL server represents your enterprise Microsoft SQL server and can be a single server or clustered server configuration. All the servers will need to have certificates and the servers with the Thin Client API and Management Studio Application Program Interface (API) will need to have a certificate with a private key. When using multiple servers for a component a load balancer is required to manage the traffic. The diagram shows multiple load balancers to show the consolidation of traffic but does not require separate load balancer for each component. Please note, the enterprise would be required to purchase and configure a load balancer based on their needs.
When setting up ShipExec for a non-enterprise environment, we still recommend a distributed installation (Figure 2). However, less servers are normally required. The SQL server represents your business Microsoft SQL server and can be a single server or clustered server configuration. All the servers will need to have certificates and the servers with the Thin Client API and Management Studio API will need to have a certificate with a private key.
When setting up ShipExec for a small volume environment, we combine as many of the component on a server as possible to maintain security (Figure 3). While it is possible to install all the components on a single server, this is not a recommended configuration. The SQL server represents your business Microsoft SQL server and can be a single server. All the servers will need to have certificates and the servers with the Thin Client API and Management Studio API will need to have a certificate with a private key.
The ShipExec™ Core and Adapters should be installed behind the company’s firewall with customers needing multiple servers with the Core and adapters installed using a load balancer to distribute traffic. The scheduler should also be installed behind the company’s firewall, but only one instance of scheduler can be used currently with the system. The Core and the Scheduler will connect to the databases.
The remaining components should be installed on the DMZ where large enterprises may need to install multiple instances of each component on separate systems with a load balancer used to distribute traffic. Once your system is configured, the ShipExec™ Management Studio may only need a single instance, unless multiple people are importing or exporting large configuration at the same time.
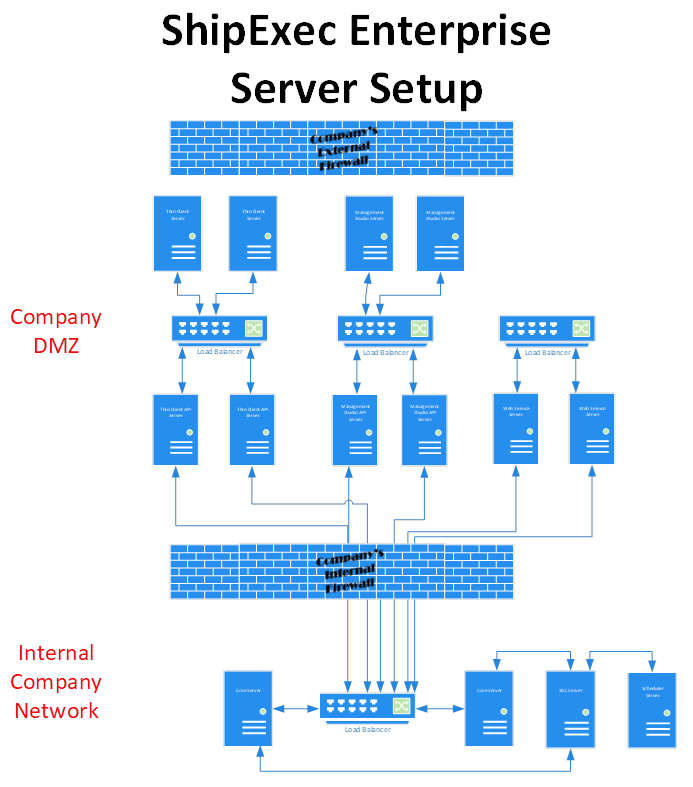
Figure 1
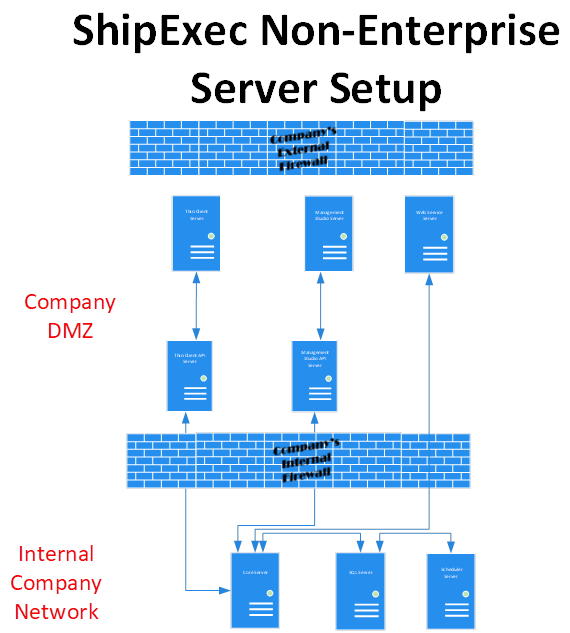
Figure 2
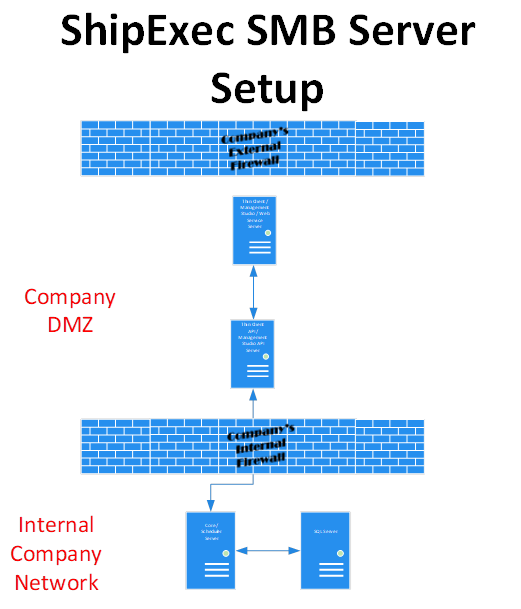
Figure 3